From Binary to Cipher: A Deep Dive into the Base of an Encipherment
In today’s digital age, data security is of utmost importance. With the increasing amount of sensitive information being transmitted and stored online, it is crucial to ensure that this data is protected from unauthorized access. One of the key components of data security is encipherment, which involves the use of encryption techniques to convert data into a form that is unreadable to anyone without the proper decryption key.
In this blog post, we will explore the basics of binary code, the role of binary code in modern computing, the evolution of encipherment techniques, the importance of cipher in data security, how binary code is translated into cipher, the different types of cipher algorithms, the advantages and disadvantages of different cipher techniques, the role of encipherment in cryptography, the future of encipherment and data security, and best practices for implementing encipherment in your organization.
Understanding the Basics of Binary Code
Binary code is a system of representing information using only two symbols: 0 and 1. It is the fundamental language of computers and is used to represent all types of data, including text, images, and videos. In binary code, each digit is called a bit, and a group of 8 bits is called a byte. Each byte can represent a number between 0 and 255.
Binary code works by assigning a unique combination of 0s and 1s to each character or piece of data. For example, the letter “A” might be represented by the binary code 01000001. To convert text into binary code, a computer uses an encoding scheme such as ASCII (American Standard Code for Information Interchange) or Unicode. These encoding schemes assign a unique binary code to each character in the alphabet, as well as to other symbols and control characters.
Examples of binary code in computing include the representation of numbers, letters, and special characters. For example, the number 5 might be represented by the binary code 00000101, the letter “B” might be represented by the binary code 01000010, and the special character “@” might be represented by the binary code 01000000.
The Role of Binary Code in Modern Computing
Binary code is used in modern computing to represent and process all types of data. It is the language that computers understand and use to perform calculations, store information, and communicate with other devices. Without binary code, computers would not be able to function as we know them today.
In addition to representing text and numbers, binary code is also used to represent images, videos, and other types of multimedia. For example, a digital image is made up of pixels, each of which is represented by a combination of 0s and 1s. The binary code for each pixel determines its color and intensity.
Binary code is also used in communication protocols, such as Ethernet and Wi-Fi, to transmit data between devices. When data is transmitted over a network, it is broken down into packets, each of which is represented by a series of 0s and 1s. These packets are then transmitted over the network and reassembled at the receiving end.
The Evolution of Encipherment Techniques
The history of encipherment techniques dates back thousands of years. The ancient Egyptians used a form of encipherment known as hieroglyphics to communicate and record information. Hieroglyphics involved the use of symbols and pictures to represent words and sounds.
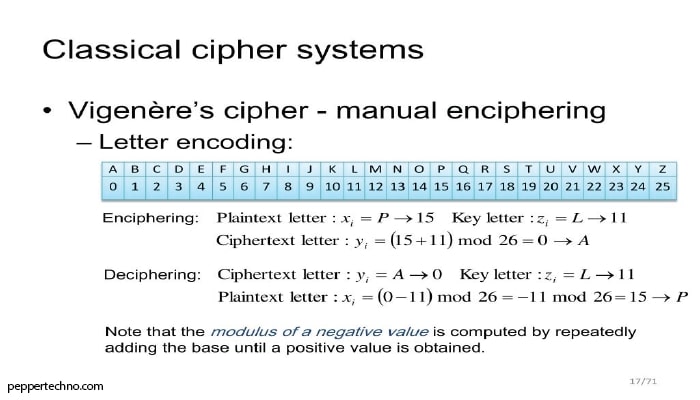
Over time, encipherment techniques became more sophisticated. In ancient Greece, the Spartans used a technique known as the Scytale to encrypt their military messages. The Scytale involved wrapping a strip of parchment around a cylinder of a specific diameter and writing the message along the length of the strip. When the strip was unwrapped, the message appeared as a jumble of letters that could only be deciphered by wrapping it around a cylinder of the same diameter.
In the modern era, encipherment techniques have evolved to take advantage of the power of computers. The development of the Enigma machine during World War II marked a major breakthrough in encipherment technology. The Enigma machine used a series of rotors and electrical connections to encrypt and decrypt messages. It was considered unbreakable until the efforts of codebreakers at Bletchley Park, including Alan Turing, successfully deciphered its codes.
Today, encipherment techniques continue to evolve as technology advances. Modern encryption algorithms, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), use complex mathematical algorithms to encrypt and decrypt data. These algorithms are designed to be secure against attacks by both brute force and mathematical analysis.
The Importance of Cipher in Data Security
Cipher plays a crucial role in data security by ensuring that sensitive information remains confidential and secure. Cipher is the process of encrypting data using an encryption algorithm and a secret key. The encrypted data, known as ciphertext, can only be decrypted back into its original form using the correct decryption key.
Cipher is used in various aspects of data security, including secure communication, secure storage, and secure authentication. In secure communication, cipher is used to encrypt data before it is transmitted over a network. This ensures that even if the data is intercepted by an unauthorized party, it cannot be read without the decryption key.
In secure storage, cipher is used to encrypt data before it is stored on a device or in a database. This protects the data from unauthorized access in case the device or database is compromised. Even if an attacker gains access to the encrypted data, they will not be able to decrypt it without the decryption key.
In secure authentication, cipher is used to protect passwords and other sensitive information. When a user enters their password, it is encrypted using a one-way hash function. The encrypted password is then compared to the stored encrypted password. If the two match, the user is granted access. This ensures that even if an attacker gains access to the stored passwords, they cannot easily determine the original passwords.
How Binary Code is Translated into Cipher
Binary code is translated into cipher using encryption algorithms. An encryption algorithm is a mathematical formula that takes a plaintext message and a secret key as input and produces a ciphertext message as output. The encryption algorithm uses the secret key to perform a series of mathematical operations on the plaintext message, which scrambles the data and makes it unreadable.
The process of translating binary code into cipher involves several steps. First, the binary code is divided into blocks of a fixed size, typically 64 or 128 bits. Each block is then encrypted using the encryption algorithm and the secret key. The resulting ciphertext blocks are then combined to form the final ciphertext message.
The encryption algorithm used to translate binary code into cipher can vary depending on the specific encryption scheme being used. Some encryption algorithms, such as AES and RSA, are widely used and considered secure against attacks. Other encryption algorithms, such as DES (Data Encryption Standard), have been deprecated due to security vulnerabilities.
Examples of how this process works in different types of technology include the use of encryption algorithms in secure communication protocols such as HTTPS (Hypertext Transfer Protocol Secure) and VPN (Virtual Private Network). In HTTPS, the plaintext data is encrypted using an encryption algorithm before it is transmitted over the internet. The encrypted data is then decrypted by the recipient using the same encryption algorithm and a matching decryption key.
The Different Types of Cipher Algorithms
There are several different types of cipher algorithms, each with its own strengths and weaknesses. Some of the most commonly used types of cipher algorithms include symmetric key algorithms, asymmetric key algorithms, and hash functions.
Symmetric key algorithms, also known as secret key algorithms, use the same key for both encryption and decryption. This means that the sender and the recipient must share the same secret key in order to communicate securely. Examples of symmetric key algorithms include AES, DES, and 3DES (Triple Data Encryption Standard).
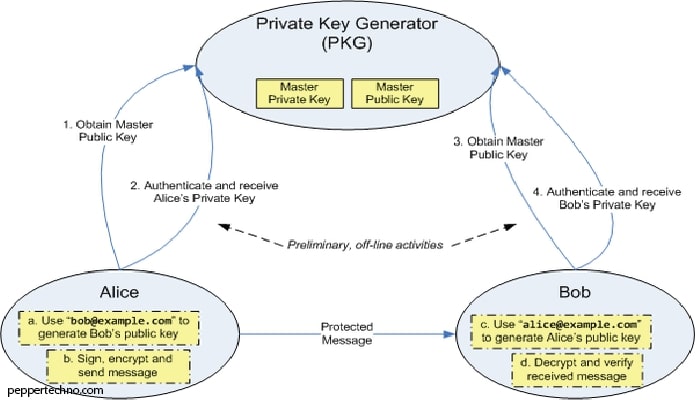
Asymmetric key algorithms, also known as public key algorithms, use a pair of keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, while the private key must be kept secret. When a sender wants to send an encrypted message to a recipient, they use the recipient’s public key to encrypt the message. The recipient then uses their private key to decrypt the message. Examples of asymmetric key algorithms include RSA and Diffie-Hellman.
Hash functions are a type of cipher algorithm that is used to generate a fixed-size hash value from an input of any size. The hash value is unique to the input data, which means that even a small change in the input data will result in a completely different hash value. Hash functions are commonly used in password storage and digital signatures.
The Advantages and Disadvantages of Different Cipher Techniques
Each type of cipher technique has its own advantages and disadvantages, which make them suitable for different use cases. Symmetric key algorithms are generally faster and more efficient than asymmetric key algorithms, making them ideal for encrypting large amounts of data. However, symmetric key algorithms require the sender and the recipient to share the same secret key, which can be challenging to manage in large-scale systems.
Asymmetric key algorithms, on the other hand, provide a higher level of security because the private key is never shared or transmitted. This makes them suitable for secure communication over untrusted networks. However, asymmetric key algorithms are generally slower and less efficient than symmetric key algorithms, which makes them less suitable for encrypting large amounts of data.
Hash functions provide a fast and efficient way to generate a fixed-size hash value from an input of any size. This makes them ideal for password storage and digital signatures. However, hash functions are one-way functions, which means that it is computationally infeasible to determine the original input data from the hash value. This makes them unsuitable for encryption and decryption.
The Role of Encipherment in Cryptography
Encipherment plays a crucial role in cryptography, which is the science of secure communication. Cryptography involves the use of encipherment techniques to protect sensitive information from unauthorized access. It encompasses a wide range of techniques, including encryption, decryption, digital signatures, and secure key exchange.
Encryption is the process of converting plaintext data into ciphertext using an encryption algorithm and a secret key. Decryption is the process of converting ciphertext back into plaintext using the same encryption algorithm and the correct decryption key. Encryption and decryption are the fundamental building blocks of secure communication.
Digital signatures are used to verify the authenticity and integrity of digital documents. A digital signature is created by encrypting a hash value of the document using the sender’s private key. The recipient can then verify the digital signature by decrypting the encrypted hash value using the sender’s public key and comparing it to a newly computed hash value of the document.
Secure key exchange is the process of securely exchanging encryption keys between two parties. It is a critical component of secure communication because if an attacker can intercept and tamper with the encryption keys, they can potentially decrypt the encrypted data. Secure key exchange protocols, such as Diffie-Hellman, use encipherment techniques to ensure that the encryption keys are exchanged securely.
The Future of Encipherment and Data Security
The future of encipherment and data security is likely to be shaped by advancements in technology and the increasing sophistication of cyber threats. As computing power continues to increase, encryption algorithms will need to become more complex and secure to withstand attacks by brute force and mathematical analysis.
Quantum computing is one area of technology that has the potential to impact encipherment and data security. Quantum computers have the ability to perform certain types of calculations much faster than classical computers, which could potentially break many of the encryption algorithms currently in use. However, researchers are actively working on developing quantum-resistant encryption algorithms that can withstand attacks by quantum computers.
Another area of technology that could impact encipherment and data security is artificial intelligence (AI). AI has the potential to improve the efficiency and effectiveness of encryption algorithms by automatically adapting them to changing threats. AI can also be used to detect and respond to security breaches in real-time, helping to prevent unauthorized access to sensitive information.
Best Practices for Implementing Encipherment in Your Organization
Implementing encipherment in your organization is crucial for protecting sensitive information from unauthorized access. Here are some best practices to consider when implementing encipherment:
- Use strong encryption algorithms: Choose encryption algorithms that are widely recognized and considered secure against attacks. AES and RSA are examples of widely used and secure encryption algorithms.
- Use long and complex encryption keys: Use encryption keys that are long and complex to make them more difficult to guess or crack. The longer the key, the stronger the encryption.
- Regularly update encryption keys: Regularly update encryption keys to minimize the risk of unauthorized access. This is especially important if a key has been compromised or if there is a suspicion of unauthorized access.
- Implement secure key exchange protocols: Use secure key exchange protocols, such as Diffie-Hellman, to securely exchange encryption keys between parties. This helps to prevent interception and tampering of the encryption keys.
- Implement multi-factor authentication: Use multi-factor authentication to add an extra layer of security to the encryption process. This can include something the user knows (such as a password), something the user has (such as a smart card), or something the user is (such as a fingerprint).
- Regularly update encryption software: Regularly update encryption software to ensure that you are using the latest security patches and updates. This helps to protect against newly discovered vulnerabilities and exploits.
- Train employees on encryption best practices: Provide training to employees on encryption best practices, including how to use encryption software correctly and securely. This helps to ensure that encryption is implemented consistently and effectively throughout the organization.
Conclusion
In conclusion, encipherment plays a crucial role in data security by ensuring that sensitive information remains confidential and secure. Understanding the basics of binary code, the role of binary code in modern computing, the evolution of encipherment techniques, the importance of cipher in data security, how binary code is translated into cipher, the different types of cipher algorithms, the advantages and disadvantages of different cipher techniques, the role of encipherment in cryptography, the future of encipherment and data security, and best practices for implementing encipherment in your organization is essential for protecting sensitive information from unauthorized access. By implementing encipherment techniques and following best practices, organizations can safeguard their data and ensure the privacy and security of their customers and stakeholders.